.
PUM
MANAGING PRIVILEGED USERS IS ESSENTIAL
*According to the Verizon 2019 Data Breach Investigations report
** According to the 2020 Cost of Insider Threats: Global Organizations report by
the Ponemon Institute
Insider threats are dangerous. Privilege misuse is devastating.
In order to avoid risking your money and reputation, you need to create and maintain an actionable system for monitoring and controlling privileged users – most powerful insiders in your infrastructure. Kriptone is the perfect solution for this challenging task.
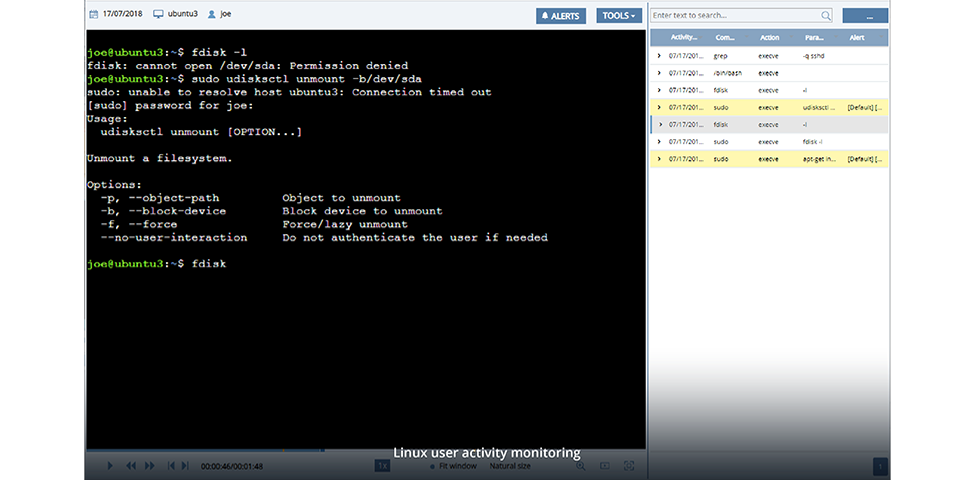
MONITOR, AUDIT, ACT
Privileged Access Management
Secure critical assets with two-factor authentication, one-time passwords, and personalization of shared accounts. Boost the protection of your network by integrating the platform with your internal ticket system.
Privileged Account and Session Management
Get full control over the sessions initiated from your jump servers, restrict or grant permissions, deliver temporary credentials for allowed RDP sessions via the secure password vault.
Real-time Incident Response
Ensure quick and effective reaction to security incidents by setting targeted alerts and specific rules for automatic response actions or manage particular cases manually. Use live session view to actually see what’s happening.