.
PAM
The Challenge
Insecure privileges
are always venerable for attacks. To resist any kind of attacks & leakage,
internal/ external, Kntrol privileged access Management (PAM) provides the
best protection mechanism and it ensures that you have complete control in
tackling any challenges.
With Kntrol:
-
Your critical endpoints are safe & secure
-
You can view all privileged accounts & monitor them
-
Permission of access to accounts in within your control
-
You can audit and monitor any activity in the privileged accounts
-
The software also helps ensure compliance
OUR SYSTEM HELPS COMPANIES TO
Our solutions for Privileged access management (PAM)
Privileged access & session management
The PAM solution
helps to secure remote access to our clients. The remote access security is a
part of the least privilege best practice & it ensures complete security to
critical endpoints and manages RDP sessions of jump servers. PAM solutions abide
by the NIST guidelines and its expected of our clients that they manage the
privileges wisely.
Our PAM solutions enables you to :
-
have security of active directory environment and have secure access to it
-
Privileged users can now have access to specific endpoints
-
The time limit for access can be regulated
-
Specific users & groups can have access to temporary credentials
-
Privileged users can manage, generate, encrypt credentials automatically
No need for any
additional installation of password management software is required if you use
the our system PAM solutions. Our solutions come with the Privileged password
management mechanism inbuilt in it. The security of the delivery credentials is
guaranteed.
For any third party vendors, employees on remote basis, subcontractors, our system PAM solutions secures remote access to all your critical endpoints and the solutions have the enterprise license hence it abides by compliance.
The unique password used only one-time
You don’t require any additional credential management to have full visibility of privileged activity, have access to your sensitive/critical data across your network. With our system One Time password solution you have 100% secure inside threat prevention.
You are the master with all controls within your access. It depends up to you,
who will access, when can he access, what can he access and it also comes with a
manual approval option. One time permission can be granted by you to specific
users to access specific endpoints and at the same time monitor their sessions
in real time.
With our One time Password solution you are able to
-
Least privilege principle can be employed
-
For each session you can grant a temporary access to critical endpoints
-
Each specific user can be associated with each recorded session
-
Approved sessions can have a LIVE monitoring system
Our one time password solutions provides the best solution for granting emergency access to sensitive data and helps manage remote access for third party vendors and subcontractors.
We offer the most apt solution for announcing exigency whilst accessing most
profound and sensitive data and handling the remote access for all 3rd –party
dealers and subcontractors.
Incorporating
Ticketing Systems.
Now granting purpose-based access is possible for high-risk sessions with our ticketing system integration. It adds one more additional layer of protection to the high critical endpoints. The sessions might be initiated by internal or third-party providers, the ticketing system integration works fool proof. This system enables:
-
Ask for justification in order to access specific endpoints
-
With the current ticketing system cross-check the provided reason
Using one additional cover of protection for the most crucial endpoints while one uses the ticketing system integration proves crucial and helps wade access to most pertinent sessions that are introduced by most of the internal users and 3rd party suppliers.
What integration or incorporation of ticketing system permits?
-
Ask for proper justification for all the effort for access to pertinent endpoints
-
Double check the support offered (reasons explained) based on present ticketing procedures and system.
An automatic report is added by our system after each session is finished. This includes complete session recording via a direct link.
Leading ticketing systems including SysAid & services can now be integrated with
our system. The third-party access management to critical endpoints can be fully
controlled with this function.
As the first assembly
is over, we spontaneously create a quick report based on the session. This also
includes a smart link to the complete assembly recorded – in sync with the
corresponding ticket. This smart function will be crucial and highly beneficial
for handling the 3rd party management and procedure of critical endpoints.
Multi-factor validation
We have developed a two-factor authentication tool (2FA) that makes sure that the right eligible person can only get access to your confidential business data. This tool functions as a part of privileged identity & access management system.
This multi-factor authentication tool acts as an add on layer in the user
verification process. This when combined with time-based and one-time password
solutions, acts as a solid protective gear securing all critical endpoints. This
multi-factor solutions comes with the industry license and runs smoothly
on Mac Operating systems and windows server and windows OS.
Make sure that only the right people can access your sensitive business data
with our two-factor authentication (2FA) tool. This tool is a part of our
system’s rich set of privileged identity and access management options.
Our multi-factor authentication tool combines user credentials and time-based
one-time passwords to add one more layer of user verification for protecting
critical endpoints. This privileged identity management solution is included
with any license and runs on Windows Server and Windows and macOS endpoints.
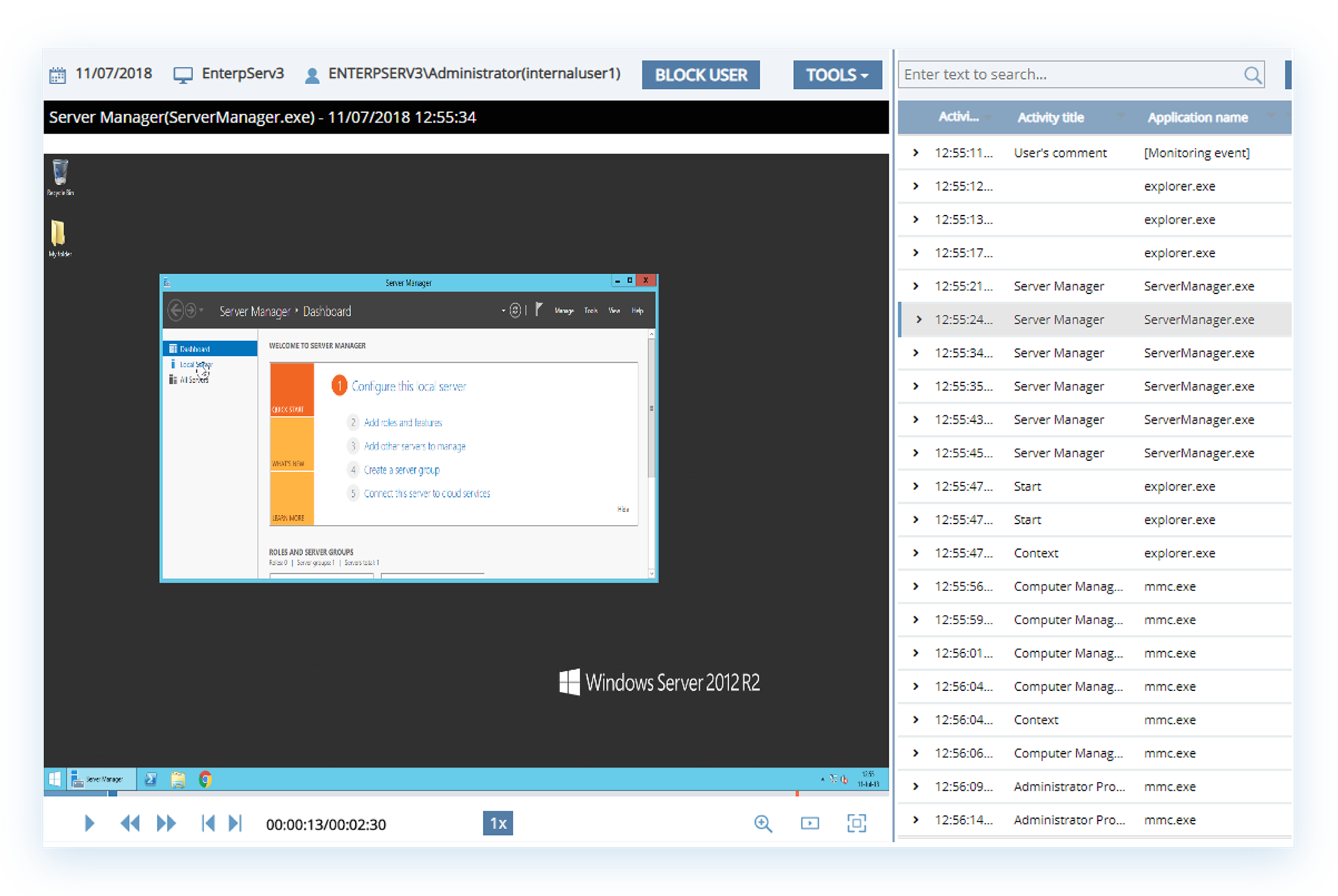
Regular observation of high privilege account
Our system arms you to regularly audit, record and monitor privileged sessions as a continuous process. In a privileged account management system, monitoring system is the key weapon to secure all critical endpoints.
In case of a loss of network, connection failure, the recording system of our
security solutions does not stop, it continues on a offline mode. All
information are automatically transferred to the server after the server network
is LIVE again, or the connection is re -established.
A large report of
user activity is generated & picked up automatically by our system and it
permits detailed analysis of daily activity.
Observing is a
critical component of restricted and confidential account handling system. We
precisely display, record and review honoured and restricted sessions.
In case the server
system is not available and is disconnected or broken or lost, Our Client shall
start tracking in its offline mode. Post restoring connection, the data and
information is forwarded to the server.
We generate all
reports, review data in an analysis format and offers clarity to all the users.
Real-time alerts & incident response
Our system’s actionable alert system adds another layer of security to the privileged activity monitoring tool. Custom targets can be set using from the wide choice of options and elaborate library of rules, mechanism also detects unusual user behaviour. The security system can be tuned to send real-time notifications, terminate applications, block users, pinpoint privilege access abuse to almost real time.
An automated incident response action mechanism can be put in place with each alert generated. This could be blockage of user access, display a warning message to the user or even kill an application.
Activate and enable
smart privilege monitoring process using the smart Alert systems.
Users can access our
vast library that explains our standard operating processes and even custom
target alerts for checking the various irregular user activities . One can block
users , terminate apps and even shoot real-time notifications to direct
privilege access misuse in future real-time access.
With regards to
alerts, one can select the options using an automated incident report and
respond action. This is of course in addition to the security staff sharing
incident alerts and forecasted warnings. Terminate an app or even restrict the
user.
Our system manages privileged access to ensure compliance
Desired level of Access management and assurance of privileged account management are the two major requirements that comes under compliance regulations. This compliance requirement can be achieved at ease with our system’s privileged access management security solutions.
To provide accurate
level of privilege account handling and access is one of the most important
demand of most of the compliance norms. The privilege access management system
supports all these compliance requirements efficiently and easily in simple
steps .
THE MOST COMPLETE SET OF SUPPORTED SYSTEMS







INTEGRATIONS